Post Quantum Cryptography in critical infrastructure sector- what's the plan for 2026?
- Raja Ravi
- Dec 27, 2025
- 2 min read
Updated: Dec 27, 2025
“A cryptographically relevant quantum computer (CRQC) will render most contemporary public key cryptography insecure.” We have seen/heard this statement in some form or the other. Some of us in the critical infrastructure industry, take a bit seriously and many ignore this. How about the adversaries planning to work or working on “harvest now, decrypt later” threat model by collecting encrypted traffic today and decrypting it once quantum capabilities mature! Let us see what we have to plan for year 2026.
Status for 2025 -
Energy systems across the Indo-Pacific are undergoing rapid digital transformation, driven by the proliferation of distributed energy resources (DERs), rooftop solar photovoltaics, battery energy storage systems, electric vehicles, and cloud-enabled grid management platforms. These systems rely extensively on public-key cryptography to provide secure device identity, authentication, software integrity, and encrypted communications between utilities, aggregators, OEMs, and consumers. Let us go one level deep at the present status of implementation of public-key cryptography
National and sector-wide Public Key Infrastructure- NEPKI framework is planned during 2026
Secure DER onboarding and device identity
IEEE 2030.5 / CSIP-AUS-based communications for DER telemetry and control
Secure firmware and software update mechanisms
What’s plan for 2025-2030 horizon?
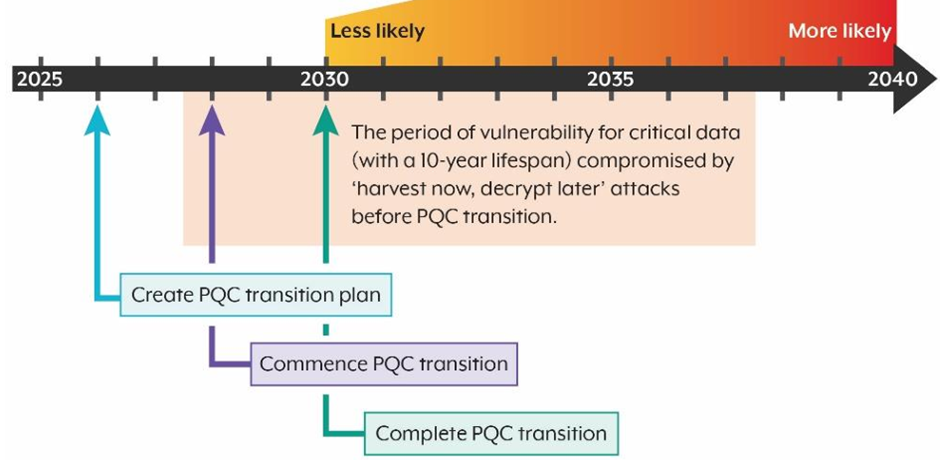
Australian Signals Directorate (ASD) has released advisory on how the organisation should plan towards Post-Quantum Cryptography (PQC). As per their suggested plan, the organisations should have a PQC transition plan in an year (2026).
Why is important now and budgeting is required?
Once quantum systems become viable, they will be capable of efficiently breaking the mathematical assumptions that underpin today’s public-key encryption and digital signature schemes—such as RSA and elliptic-curve cryptography (ECC) . A compromise of these cryptographic foundations would undermine the ability of grid operators to trust device identities, enforce operational controls (such as export limits). This is not only a cybersecurity risk but a direct operational and safety concern for power systems.
What could be approach to PQC Readiness in 2026?
I believe the present industry focus should be on readiness, awareness, and informed decision-making. The key activities include:
PQC Awareness, policy making and Risk Framing - Provide high-level guidance on when and how to begin PQC planning. Explain quantum-related cryptographic risks in energy-sector terms (identity trust, firmware integrity, DER control). Ensure utilities, OEMs, and regulators understand both the risks of inaction and realistic migration pathways.
Locate and assess Cryptographic Dependencies and assets - Identify where public-key cryptography is used within different assets like DER ecosystems, different kind of PKI frameworks, and IEEE 2030.5-based communications.
Implementation approach - Think and get the ground ready for PQC. Some readiness activities can be
Pilot hybrid TLS in non-safety-critical environments first (DER testbeds, staging). This is useful to the organisations to get ready
Build a “PQC readiness score” for assets.
Establish a quantum incident scenario in exercises: “CA compromise / certificate forgery in future world”.
Training and Capacity-Building Activities - Incorporate PQC concepts into technical workshops, user guides, and hands-on labs.
It may be valuable to develop a structured guidance document that provides clarity on how post-quantum cryptography could be introduced in practice, while closely tracking how standards bodies, government agencies, and industry alliances are shaping its adoption.




Comments